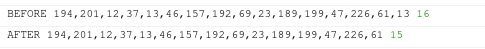
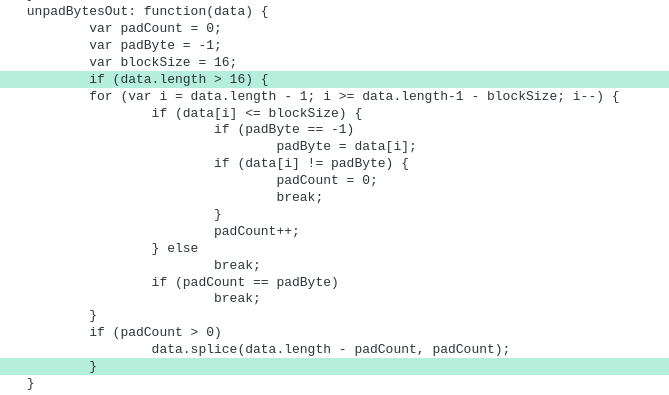
UPD: The RCPC token wall seems to have been removed. As of the time of this update, no additional security check is needed to access codeforces. Hence this script has been rendered obsolete by this change, and you will receive an error message if you attempt to run it.
As a result of a recent security update, many codeforces tools have been broken. In short, in order to access codeforces, a token is now required, which is decoded by the browser through a javascript implementation of AES. I have explained the specifics of this in my previous blog: https://codeforces.me/blog/entry/80070.
The token is different based on your IP address, and must be sent as a cookie with all requests to codeforces. Failing to do so will result in codeforces responding with a redirect page, containing the encrypted cipher token.
I have written an ad hoc script to decode this token using python.
https://github.com/great-prophet/adhoc_cf_rcpc_token_decoder
This script makes a request to codeforces to get the raw response with the AES cipher parameters, parses out the encrypted cipher, decodes it using an equivalent python AES implementation, and returns a hex formatted token. To use, simply run "source/cf_rcpc_token_decode.py" without input, with a python 3 interpreter.
Here is a screenshot of the expected behavior:
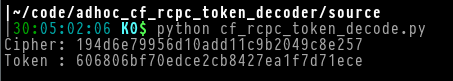
Note: You can ignore the "Cipher" output. It is the raw encrypted token, before decoding.
This token should be passed as a cookie with the key "RCPC" in all codeforces requests. For example, here is how you would do so with curl:
curl 'https://codeforces.com' -H 'Cookie: RCPC=606806bf70edce2cb8427ea1f7d71ece'
This script, by itself, will not automatically fix broken cf tools. You will need to have some technical knowledge in order to manually add the cookie as described above. This process is different for every tool. However I hope it can serve as a foundation for implementing a general fix.
Disclaimer: My current script is very very hacky and may be broken by future changes. However I will try my best to maintain it if an update does occur.